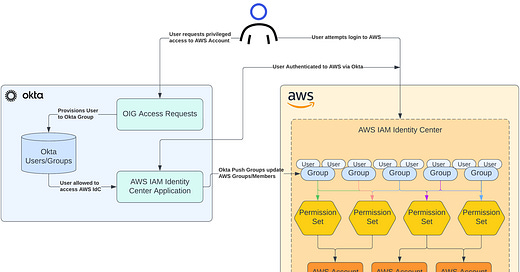
Okta and AWS Identity Center enforce JIT-privileged access
One risk IAM administrators are very familiar with is having a lack of control over credentials. Once credentials that grant privileged operations are lost or shared without permissions, they can be used to give unauthorized people elevated access to resources. A reasonable prevention strategy is to use a Just-in-Time (JIT) access model to make all access temporary by default, and reduce overall time access is granted to mission-critical systems.
For organizations that use AWS and Okta, Okta administrators can leverage the power of Okta Access Requests to grant JIT access before anyone can access AWS resources…
Keep reading with a 7-day free trial
Subscribe to IAM Radar - Identity & Access Management Industry Tracker to keep reading this post and get 7 days of free access to the full post archives.