CyberArk & Identity Security, AI Data AuthZ, PCI4 & MFA, Modern Access Request
CyberArk and the Identity Security Imperative
PAM veterans CyberArk have released a new book - all 139 pages of it - focused on Identity Security. Identity Security has emerged almost as a marketing alternative to zero trust for many vendors - with a blurring, overlapping and slack definition all adding to the market confusion.
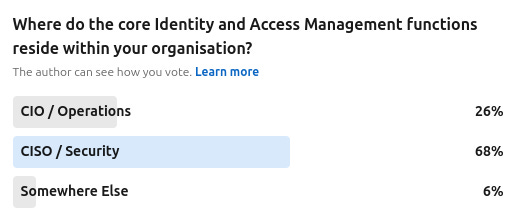
It seems the emergence of information security budget-holders taking a significant interest in the IAM world is a long standing evolution. As IAM tooling was historically productivity and compliance-led and sitting under the infrastructure/CIO umbrella the transition is interesting. Whilst the outcome of a successful governance project clearly improves an organisational security posture, the budget often did not - it was often audit or compliance. This is changing.
Image Source: The Cyber Hut Community Poll Jan 2025 n=47
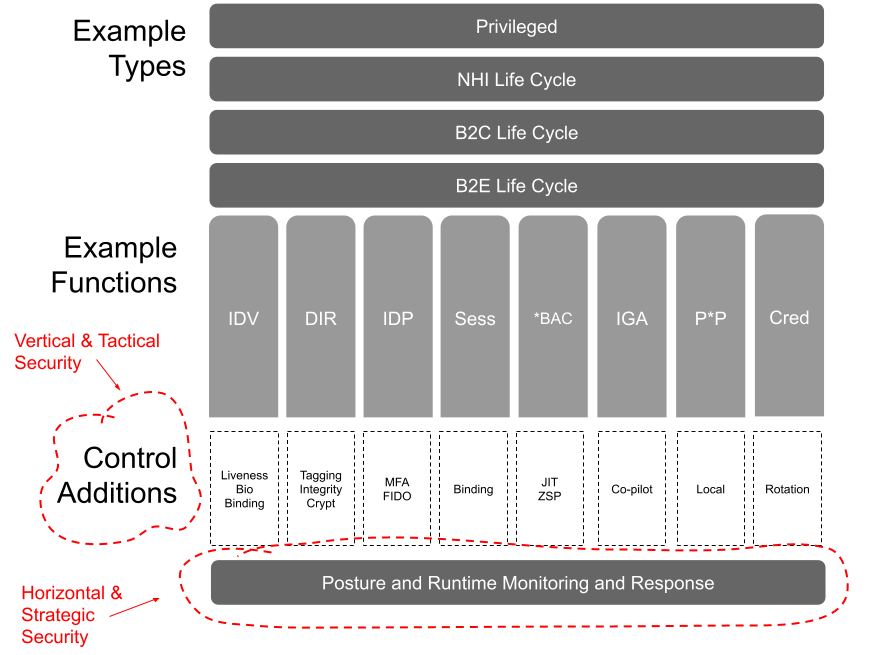
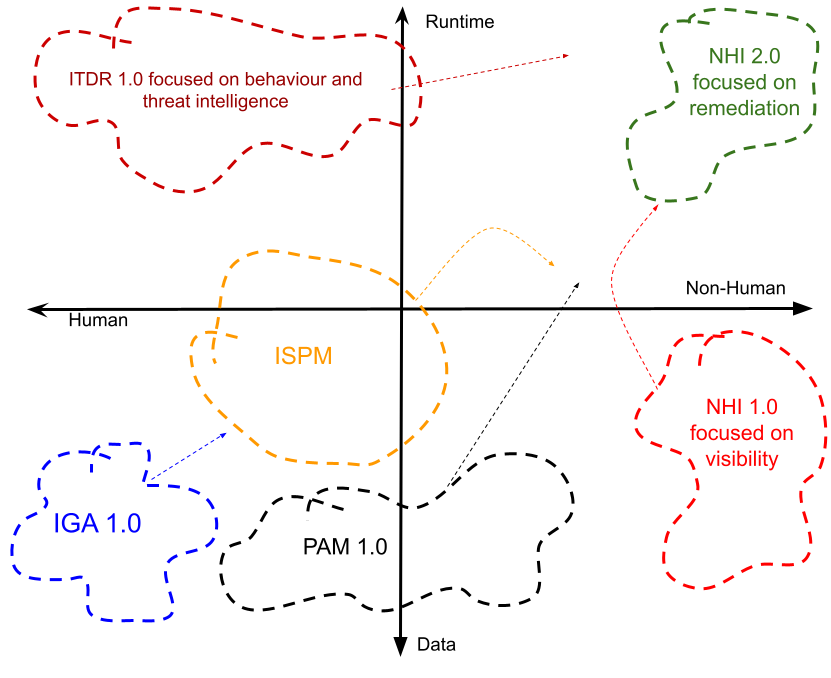
The definition of what Identity Security actually delivers is still open to debate, but it seems like there are several meta-patterns. Firstly it seems point solutions such as SSO, IDP, MFA, IGA and PAM are seen as pillars - implementing controls that are targeted and often vendor-specific. Those controls are often tied to a life cycle associated with one identity-type - customers, employees or non-human’s for example. So an MFA component for customers is unlikely to be used for a workload’s for example.
To that end we start to see a break out of functions that over lay the entire end to end life cycle of identity capabilities - from creation to off boarding - but we need to do that for both humans and non-humans.
This “security” overlay needs to also consider both identity data (posture and hygiene) as well runtime behaviours - so essentially what happens post authentication.
So why is a PAM vendor now talking about identity security? We’re starting to see numerous established identity, network and endpoint protection vendors shifting their narrative to engage in this identity security world. But can they only seemingly do so against their own pillar of influence - and also only likely for their existing customer bases - or can they do more?
Image Source: The Cyber Hut identity security view
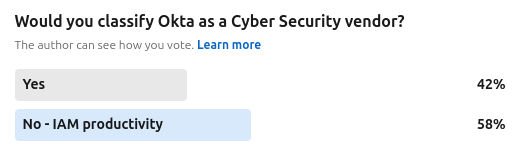
So vendor’s such as CyberArk, Sailpoint, Cisco, Crowdstrike and Okta are all delivering security-first capabilities, mission statements and marketing narratives that are sitting firmly in the security world. Those vertical extensions are perfectly valid and will enhance security for those who deploy them. The question moves of course to prospective buyers - would say the ITDR-esque capabilities from Sailpoint be used without their IGA stack? Or perhaps Okta’s ISPM features without their SSO base?
Image Source: The Cyber Community Poll Jan 2025 n=76
Image Source: The Cyber Hut - what next for Identity Security?
The CyberArk mini-book is a good overview of the some of the key challenges many organisations are now facing - a broad spectrum of identities, different stakeholder needs, more systems being integrated and of course increasing levels of risk associated with both internal and external adversarial activity.
Other resources:
The Cyber Hut Identity Security Scorecard
IAM at 2035: C-level Future Guide to Identity Security (Book coming Q2 2025)
Quick Pick Links
Bitwarden: Passkey Adoption Surges 550% in 2024 as Bitwarden Reports 1.1M New Implementations
Lumos: Lumos Launches Integration Hub, Powering App Connectivity in Minutes
Microsoft: Step-by-Step Guide : How to use Temporary Access Pass (TAP) with internal guest users
Pathlock: Pathlock Cloud Achieves More Than 100% YoY ARR Growth in 2024
Semperis: Semperis Surpasses $100M in ARR as Organisations Prioritise Identity System Defence
Veza: Modern Access Request Processes: Best Practices & What to Avoid in 2025